RESTRICTED USE AGREEMENT FOR ICT PARTICIPANTS
LANGUAGE TO BE INCLUDED IN ANY RESTRICTED USE AGREEMENT FOR ICT PARTICIPANTS:
“This is a legal agreement between you, the applicant, (the “Applicant”) and The Crucible Project, a not-for-profit corporation of Illinois (“TCP. By clicking “I Accept” at the end of this Intellectual Property Confidentiality and Non-compete Agreement (the “Agreement”), you acknowledge that you have read, understand, and agree to be bound legally by the terms and conditions of this Agreement.
If you do not agree with this Agreement, you may not submit an application, and you are not granted permission by TCP to volunteer for, participate in, observe, review, or otherwise access any Confidential Information and/or Protected Information under TCP control, or through TCP events/activities.
You shall be bound to this agreement as of the date and time of your application submission to TCP for consideration (the “Effective Date”). You may, and are encouraged to, print this Agreement for your own records.
The Contractor and TCP, referred to individually as a Party (a “Party”), or collectively as the Parties (the “Parties”), for good and valuable consideration, the sufficiency and receipt of which is hereby acknowledge, do hereby agree to the following:
Confidential Information of TCP includes, but is not limited to the (1) business plans, methods, practices; (2) personnel, volunteers, supporters, suppliers; (3) services and programs, documentation, manuals, specifications, techniques, methods, presentation, exercises, activities; (4) inventions, processes, methods, products, copyrights, trademarks, intellectual property, intellectual property applications, certain Copyrighted Works leased from Shadow Work Licensing, LLC (“SWL”), a Colorado partnership, and other technical and/or proprietary information (the “Confidential Information”).
In addition to Applicant’s access to the Confidential Information, through the course of attending, observing, providing, presenting, and/or experiencing the services of TCP (the “Activities”), it may become necessary for TCP to share, disclose, or otherwise allow access by the Applicant to other materials TCP asserts as confidential, including the identity of participants in certain programs, as well as the activities, experiences, and actions of participants, which, due to the mental, emotional and/or spiritual components are considered personal and shared in the bonds of secrecy with other program participants (exclusive of the Confidential Information designated as the “Protected Information”).
Applicant understands that the experiences of each participant are personal, emotionally significant, and shall be considered private between those sharing the experiences of the Activities. As part of this Agreement, and in exchange for the shared experience and agreement to a duty of confidentiality by other participants, the Applicant shall not disclose, and will undertake all reasonable efforts to keep confidential the Protected Information, including but not limited to, specific details of activities, and the actions and identities of other participants which Applicant witnessed, experienced, or otherwise was made aware through participation in the Activities. This duty of confidentiality shall be indefinite, unless specifically released/authorized in writing by each affected participant, or to the extent that specific information becomes public by the lawful public release of any other participant.
The Applicant shall take all reasonable action to protect the confidentiality of the Confidential Information and any other Protected Information from disclosure without written approval from TCP. An example of written approval would be the written approval to facilitate Carpet processes in TCP Events, using the Confidential Information. You shall protect such Confidential Information and Protected Materials from any unauthorized or inadvertent disclosure to a third party using the same care and diligence that the Applicant uses to protect its own proprietary and confidential information, but in no case less than reasonable care. The Applicant shall ensure that each of its employees, officers, directors, or agents who has access to Confidential Information disclosed under this Agreement is informed of its proprietary and confidential nature and is required to abide by the terms of this Agreement. The Applicant, as the receiver of Confidential Information disclosed under this Agreement, shall promptly notify the disclosing Party of any disclosure of such Confidential Information in violation of this Agreement or of any subpoena or other legal process requiring production or disclosure of said Confidential Information.
All Confidential Information disclosed under this Agreement shall be and remain the property of TCP, except for the Copyrighted Works leased from SWL, and nothing contained in this Agreement shall be construed as granting or conferring any rights to such Confidential Information on any other party. The Applicant shall honor any request from TCP to promptly return or destroy all copies of Confidential Information disclosed under this Agreement and all notes related to such Confidential Information. The Parties agree that TCP, SWL and the participants of Activities will suffer irreparable injury if its Confidential Information is made public, released to a third party, or otherwise disclosed in breach of this Agreement and that TCP, for itself or on behalf of one or more participants of Activities, shall be entitled to obtain injunctive relief against a threatened breach or continuation of any such breach and, in the event of such breach, an award of actual and exemplary damages from any court of competent jurisdiction.
The terms of this Agreement shall not be construed to limit either Party’s right to develop independently or acquire products without use of the other Party’s Confidential Information. The disclosing party acknowledges that the Applicant may currently or in the future be developing information internally, or receiving information from other parties, which may be similar to the Confidential Information. Nothing in this Agreement will prohibit the Applicant from developing or having developed for it products, concepts, systems or techniques that are similar to or compete with the products, concepts, systems or techniques contemplated by or embodied in the Confidential Information provided that the actions contain no Copyrighted Works of SWL and are beyond the time limit agreed to, of two years, and the Applicant does not otherwise violate any of its other obligations under this Agreement in connection with such development.
Notwithstanding the above, the Parties agree that information shall not be deemed Confidential Information and the Applicant shall have no obligation to hold in confidence such information, where such information: (a) Is already known to the Applicant, having been disclosed to the Applicant by a third party without such third party having an obligation of confidentiality to the disclosing Party; or (b) Is or becomes publicly known through no wrongful act of the Applicant, its employees, officers, directors, or agents; or (c) Is independently developed by the Applicant without reference to any Confidential Information disclosed hereunder; or (d) Is approved for release (and only to the extent so approved) by the disclosing Party; or (e) Is disclosed pursuant to the lawful requirement of a court or governmental agency or where required by operation of law.
The parties agree that, to the extent required by applicable local, state, and federal laws, the services provided under this Agreement will comply in all material respects with legal regulations, rules, or orders applicable to the services provided herein, including but not limited to regulations promulgated under Title II of the Health Insurance Portability and Accounting Act, commonly referenced as HIPAA.
Nothing in this Agreement shall be construed to constitute an agency, partnership, joint venture, or other similar relationship between the Parties.
Neither Party will, without prior approval of the other Party, make any public announcement of or otherwise disclose the existence or the terms of this Agreement.
Non-disclosure provisions and the Parties duties to protect Confidential Information and/or Protected Information shall survive the termination of this Agreement and shall remain in effect until the Confidential Information and/or Protected Information is legally disclosed through any other means, or written release is received by the Party. You further agree that your breach of these duties could cause irreputable harm and damage to goodwill, which may be difficult or impossible to ascertain, and that the remedies at law for any such breach will be inadequate. Accordingly, you agree that in the event of an anticipated, threatened, or actual breach, in addition to any other remedy which may be available at law or equity, TCP or SWL, for itself or others affected, shall be entitled to specific performance and injunctive relief.
This Agreement is intended to be as broad and inclusive as permitted by any applicable laws. If any portion of the Agreement is held invalid, the remainder of the Agreement will still continue in full legal force and effect.
The requirement to protect Confidential Information disclosed under this Agreement shall survive termination of this Agreement.
Should a dispute arise regarding this Agreement, Parties agree to attempt resolution of the dispute first by utilizing mediation in accordance with the rules of the American Arbitration Association (AAA), or any other mutually agreed format prior to litigation. In the event litigation occurs, all parties agree and consent to the jurisdiction of the circuit courts of Cook or DuPage Counties in the State of Illinois, and that disputes shall be settled by application of the laws of Illinois without regard to the conflict of law rules of Illinois.
Summary of “SWL Elements” in the TCP manuals,
which are copyrighted by Shadow Work Licensing, L.L.C. (“SWL”)
The following “SWL Elements” are shown in green typeface. These SWL Elements may not be translated or modified in any way without permission from Shadow Work Licensing. If you wish to modify one of these SWL Elements, please contact the TCP leadership to begin the process of gaining permission from SWL before you begin translating or otherwise modifying these Elements.
The following is only a summary, which does not show the context for many of the Elements, nor does it show where each Element is located in a TCP Manual. A complete listing of all the SWL Elements, and their locations in the TCP Manuals, is available upon request from TCP or SWL. The complete listing exists in the “Standards and Specifications Rider to the Copyright License Agreement Between Shadow Work Licensing LLC. and The Crucible Project”.
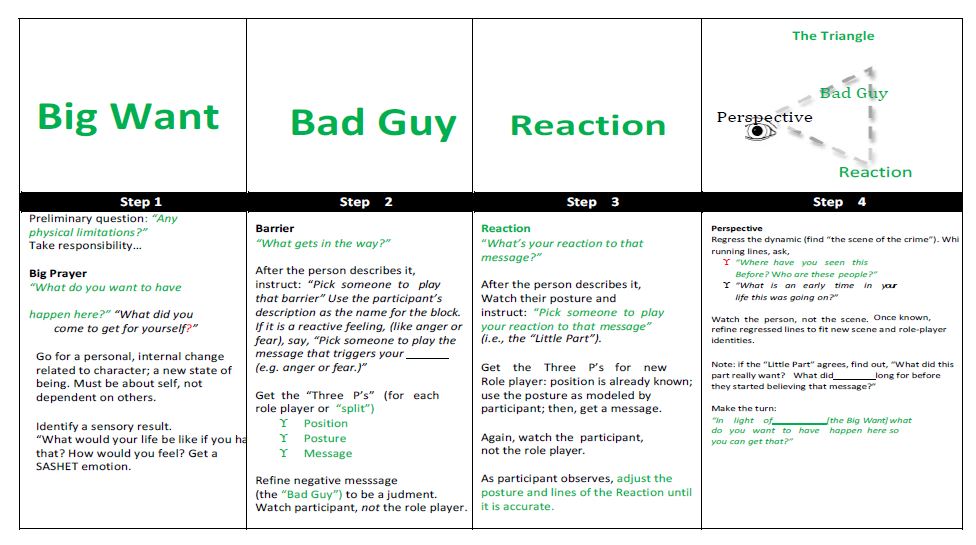
PRE-PROCESS:
- Ask safety questions
- Any physical limitations?
- asking the questions alerts people that we care about their safety emotionally
- Big Want
- What do you want to have happen here?
- “lead from a step behind”
- clear want should Not be dependent on other people
- What would you have for yourself?
- If you had that __________ (e.g., a better job), what would it give you that you don’t have now?
- Positive “want
- if they say, “I don’t want to be…” , what’s the positive thing you do want
- Bad Guy
- What gets in the way?
- What is it that keeps you from getting [the man’s want]
- Role player (pick a man to play; are you willing to play this role)
- What does the [name of block] say to you?
- message that is juicy
- remove specific references to roles, ages, time and place. If the message says, “you’re a lazy husband” ask if the role-player can generalize it to say “you’re lazy” (later, when you are regressing the message, it will be easier for there to be a younger version of “you’re lazy” but harder to make that connection if the participants hears the words lazy husband.)
- If a criticism is a question, e.g., “why can’t you do anything right?” see if participant can come up with the implied answer.
- ask, when that part says, “why can’t you do anything right”, what is the answer to that question?
- What is it about you, that you [action he named]?
- if it says “I …” trying switching it to “you …” so the participant gets the direction of the criticism
- Reaction
- What’s your reaction to that message?
- get the reaction message before pulling the person out.
- “ pick someone to play your reaction to that message”
- get the position
- posture
- message
- adjust the posture and lines of the reaction until it is accurate
- Regression to find source of dynamic:
- Where have you seen this before?
- Who are these people?
- What is an early time in your life that something like this was going on?
- Where you saw/heard/felt this dynamic
- So, in light of [the big want], what do you want to have happen here so you can get that?
- Avoid the language “what needs to happen here”—this tends to steer the participant toward support work
Best practices:
- watch the participant, not the role players.
- exact words and use them—mirroring back what they say lets them know that we are paying attention
- put any ideas you have early on “in your back pocket”
Split
Triangulated position
- Come stand here (point) so you can see both parts
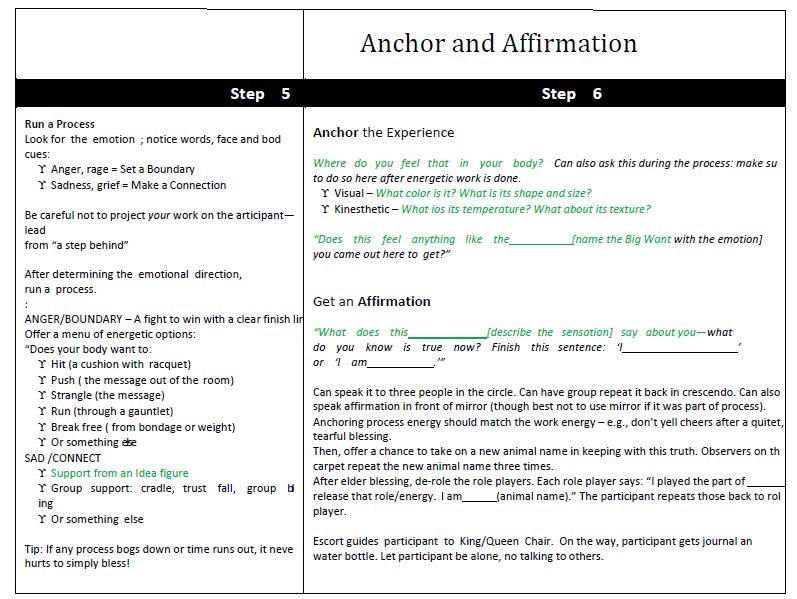
Run A Process:
- determine direction
- support man determining how to work on the dynamic to get what he wants
- set up and run the work the man has chosen
- confirm work is complete
Anchor New Energy/Result:
- Where do you feel that in your body?
- What color is it?
- What is its shape and size?
- What is its temperature?
- What about its texture?
- Does this feel like the, [name the Big Want]
Affirmation choose and own new affirmation about himself:
- What does this [describe the sensation] SAY ABOUT YOU—
- with “-ed” endings
Anchor New Energy/Result:
- Warrior Run
- Shadow Reversal
- Person wants to do anger work but energy is flagging toward the bad guy. They need to get the energy out of the bad guy—to become them for just a minute, to feel the power of that part—then take that energy back into the work they were doing and use it against the bad guy. This is a short sub-routine that happens during a warrior run but doesn’t alter the overall direction of the process.
- Do a shadow reversal to help participant get the power from bad dad to use against bad dad.
- Good Guy/Bad Guy
- Do you want to hit, push it out, beat it down, strangle it, or something else?
- Make it hard enough: “a fight they can win.”
- Place staff men as safety on the man, enough staff to provide resistance. They will allow the man’s arms to be free, and hold him under his arms, to prevent his moving forward
- Set up stack of cushions covered by blankets to hold them still.
- Have the role player begin saying his lines, then have the man begin hitting with an object / punching with his hands / strangling.
- Establish the path and the finish line for the pushing and “aim” the man working toward the finish line with the bad role player in the way.
- Split out good [dad] with another role player so only the bad dad gets silenced.
- Get support from a good dad or another ideal encourager.
- If the participant is chatty, direct them to use just sounds and growls, no words
- Where do you feel that in your body?
- What will it look like when it is done/gone/out of your life
- Is it finished?
- The role player will slowly go down to the ground
- Can pause near the end and ask the man what is risky about finishing this message.
SOVEREIGN (Support):
- Ideal Support
- God Split
- participant has projected negative messages on god based on messages from important people in life.
- The Sovereign connects from “above” by being strong and caring for, and the lover connects from “underneath” by being vulnerable and being cared for.
- Was there anyone who could have given [seven] the kind of support he/she wanted?
- From who did [seven] want the support he/she never got?
- Would you be willing to be an ideal mom/dad and bring to seven what he/she always wanted
- Speak slowly, repeat things, use the word “and” a lot, tell participant what is coming.
- What did [seven] always want to hear from mom/dad? And what qualities do you see in seven? And what might you say that seven always wanted to hear? And is there a kind of touch seven would like?
- Have the man model the support (unless using cradle or not perform process)
- Have the man receive the support
- with your eyes, and your touch, and your words of BLESSING?
- Repeat phrases aloud to slow it down
- eyes, touch, words
- Would you be willing to switch places now and receive this support from the other side
- You can also bring back criticisms made earlier by the “bad guy” part, and say, this little girl heard she was ___________.
What’s At Risk And Risk Manager:
- What is it about her that
- Participant is having a hard time taking a risk—in general in their life, or specially while out on the carpet (with some aspect of the process itself); in trying to keep the person safe, this part of them is also keeping them stuck and blocked. this is a sub-routine that can happen at any point during a process; it is usually used to get over a hurdle so the main process can resume but it can also be the complete process.
- What do you get out of keeping this weight/block in your life? (tease out an answer)
- What might you lose or what bad thing might happen if you got rid or it? (tease out a risk)
- What does it cost you to have this weight/block in your life? (tease out cost)
LOVER (Support):
- Lost Loved One
- Tombstone
- Participant is burdened by a painful way of doing life learned from someone important to them—they unconsciously stay connected to that person (who could be living or dead) by carrying on a tradition or pattern learned from that person, seeking their approval, validation or trying to heal them
- Whatever the issue, it’s all done out of deep love. The problem is, this painful way of trying to stay connected to their loved one is not working, and is getting in the way of their well- being now.
- Frame the role player as playing only all the good/gold parts of the lost person, who they were, in their heart of hearts.
- Have the man kneel next to the grave and pull back cloth when ready.
- Would you be willing to switch and receive this BLESSING?
MAGICIAN:
- Predator Process
- Participant has a part of themselves that they judge is “bad” and they are trying to not be that way but keep slipping back; in trying so hard to not be like someone that hurt them, they have lost their power to do the good they want to do.
Facilitator Shadows:
- a “perfect” process
- finish the process in record time
- prove myself in the process
- facilitate from my skill, genius and/or intuition alone
- run this process by myself
- credit for the power of this process
- I will step in and “save” this process
- emotional, life changing process
- get it all right now
- fall in love with me
- prove the healing power of my love
- live on the cutting edge
- an emotional fix for myself out of the process
- control the process
- I know how the process will end
- blame the participant for not doing their work right
- break them down with shame
- be the ordeal in the process
